Cloud computing adoption has been rapidly on the rise, so much so that it now looks set to become a dominant solution for both the business and personal computing needs of the future.
But what about cloud security?
Just a few years ago, most people considered the cloud a dark mystery yet today the term “cloud computing” is used in a very positive light, with more and more businesses migrating their mission critical operations to the cloud.
Widespread adoption is not surprising given the benefits in scalability, flexibility and reduction in TCO (total cost of ownership). The cloud is already widely recognised as the preferred software delivery model for common enterprise applications and investment managers are accelerating the adoption of cloud infrastructures to power their asset management operations.
The question of cloud adoption in asset management is no longer a question of “if” but “when.”
Since 2002, when Kurtosys first began to transform the way that financial information is shared and consumed, we’ve relished the challenge of using cutting edge technology to solve problems, cut waste and inefficiency and make life easier for both asset managers and their clients.
Technological innovation has changed the course of asset management, helping firms attack margin compression head on with intelligent, tech-based solutions that cut costs while simultaneously enhancing the client experience. But of course new technology also brings its own set of risks and compliance conundrums.
Which cloud security risks prompt the greatest concern?
When it comes to cloud computing, security has been the main source of skepticism. Especially in its infancy, the cloud provoked fears over the safety of client data and the security of hosting business-critical systems in what was essentially, back then, unchartered territory.
Even in 2013 with cloud security hugely improved, data protection dominates the lists of concerns: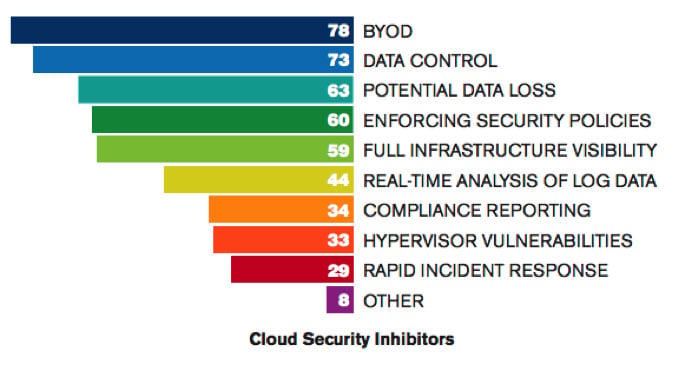
Source: Accelops Cloud Security Survey 2013
Aside from the obvious challenges posed by “Bring Your Own Device” (BYOD) which leaves IT managers struggling to control security across a myriad of personal devices brought into the workplace by employees more focused on usability than security, data control and potential data loss were named as the greatest inhibitors to effective cloud security by respondents in the Accelops Cloud Security Survey 2013.
Yet, despite nagging concerns, the vast majority of firms feel confident when it comes to cloud security. In fact, just 18% say their existing cloud security tools are inadequate to ensure security and regulatory compliance.
Cloud security is not the same everywhere so do your research
That’s good news, but even amidst all the positivity, it’s important to remember that security in the cloud isn’t a case of one-size-fits-all. Security isn’t about securing the cloud; it’s about securing the cloud-based services that reside on the cloud.
How service providers manage security is critical so it’s essential to choose a provider with the ability to guarantee security in a way that’s relevant to your business requirements.
That’s why we’ve put security front and center of our business. We take the security of our client’s data extremely seriously and assess each individual project to ensure we approach security in a tailored, personalised way.
We work closely with every client to determine their individual data security requirements and quickly establish confidence in our security management measures. Our products and services include comprehensive security controls built in to ensure data protection — and we also provide options such as two-factor authentication which can be added to fit client security risk and business requirements.
How to check out a cloud vendor’s security credentials
Embedding effective security has become second nature at Kurtosys, but unfortunately, that’s not the case everywhere. Half of the companies surveyed by Ponemon Institute, an independent research firm, reported that they had not taken security risks into account when striking cloud deals.
Talking to the LA Times, Thomas Trappler, a highly experience IT security advisor, said:
What most of us are used to is “I buy it, I maintain it. If something’s broken, I can beat on someone’s door and get them to fix it.” Now “it” and “someone” are far away “and the question is, how do I ensure they do it right.
How do you check out the security credentials of the IT vendors you are considering doing business with?
According to Trappler, these questions should come close to the top of your list:
- What encryption methods are used?
- What’s the reliability of the storage computers?
- Are background checks of the cloud provider’s employees carried out?
Cloud services can offer security that is just as good, if not better, than a standard setup, but it’s crucial to do your homework. While the cloud removes inefficiency and wastage in droves, it also reduces control and that’s an important change that affects every aspect of IT management. When you embrace this change and are realistic about both the risks and benefits of cloud services, you’ll reap the rewards. But like most things in life, some hard work put in at the beginning to establish secure processes will pay dividends for years to come.



